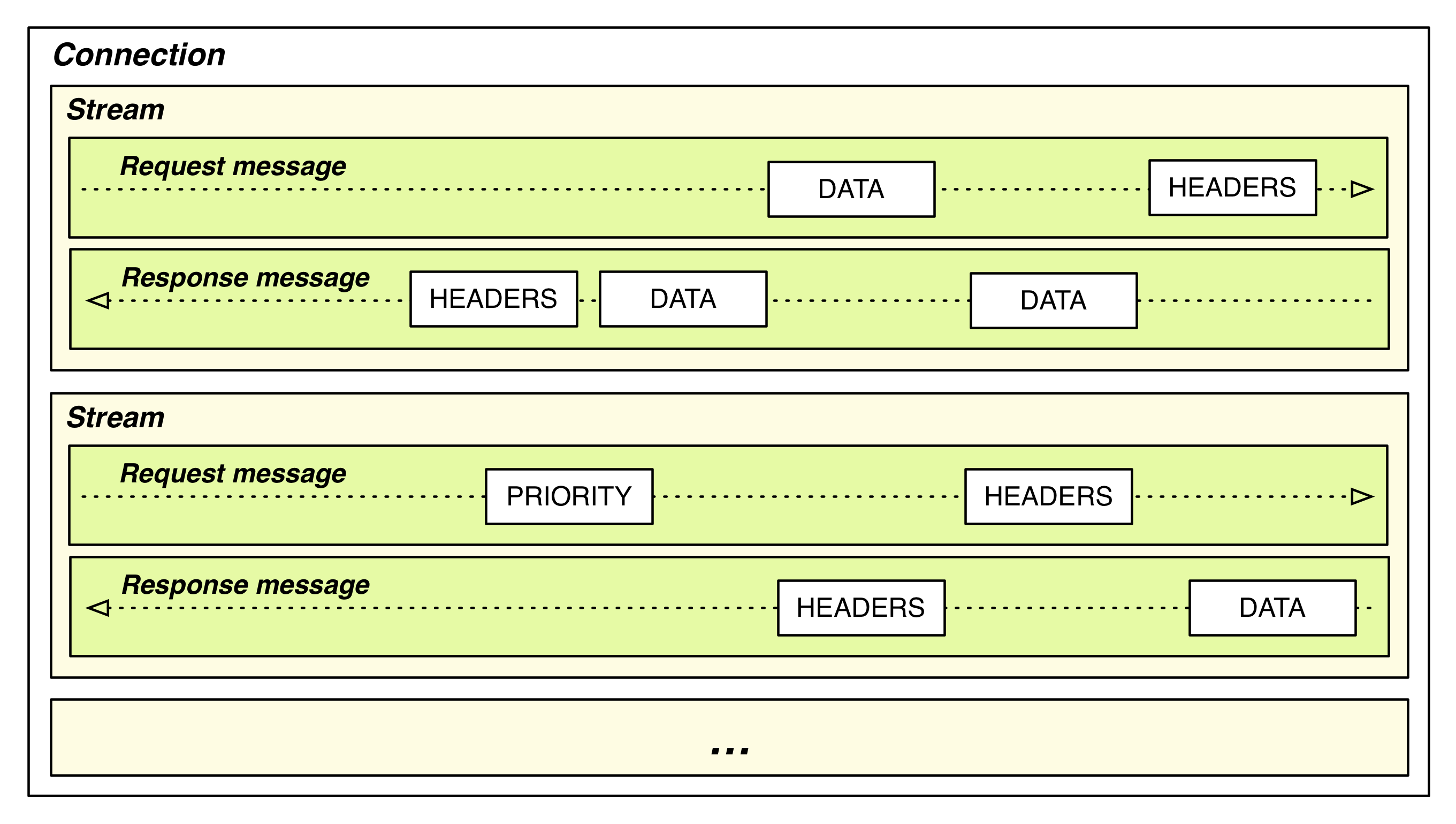
HTTP/2 在没有破坏原有的语义化(例如:方法、状态码、URIs、首部字段……)的基础上,更改了数据的封装格式以及客户端和服务器之间的数据传输机制,引入了二进制分帧层(Binary Framing)采用新的编码机制,客户端与服务器之间的通信信息被分割成更小的帧,每个帧都是二进制编码。本文将对 HTTP/2 和 HTTP/1.1 的差异部分进行对比,同时对 HTTP/2 部分关键帧进行梳理说明。
显示部分
REQUEST
HTTP/2 VS HTTP/1.1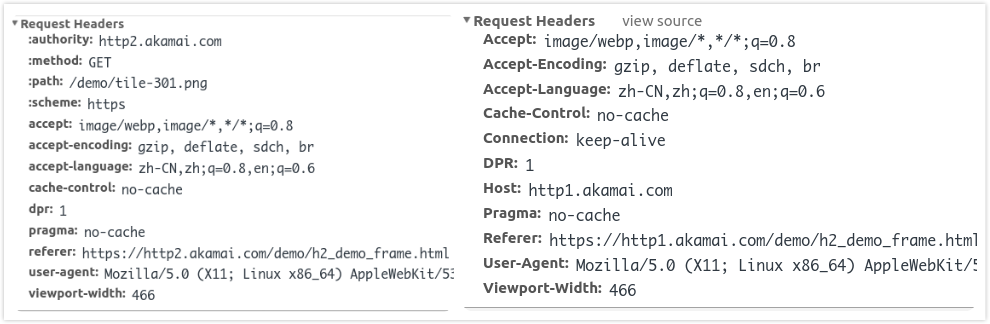
HTTP/2 Header部分新增冒号开头 authority method path scheme 首部,同时所有字段均小写
RESPONSE
HTTP/2 VS HTTP/1.1
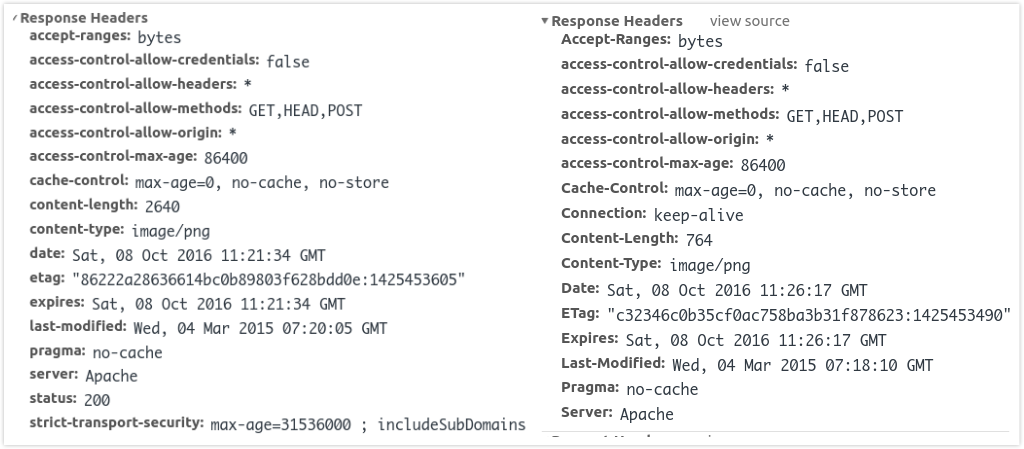
所有字段均小写,其余基本相同
流量部分
调试工具:
- Chrome net-internal
- Wireshark
Chrome net-internal:
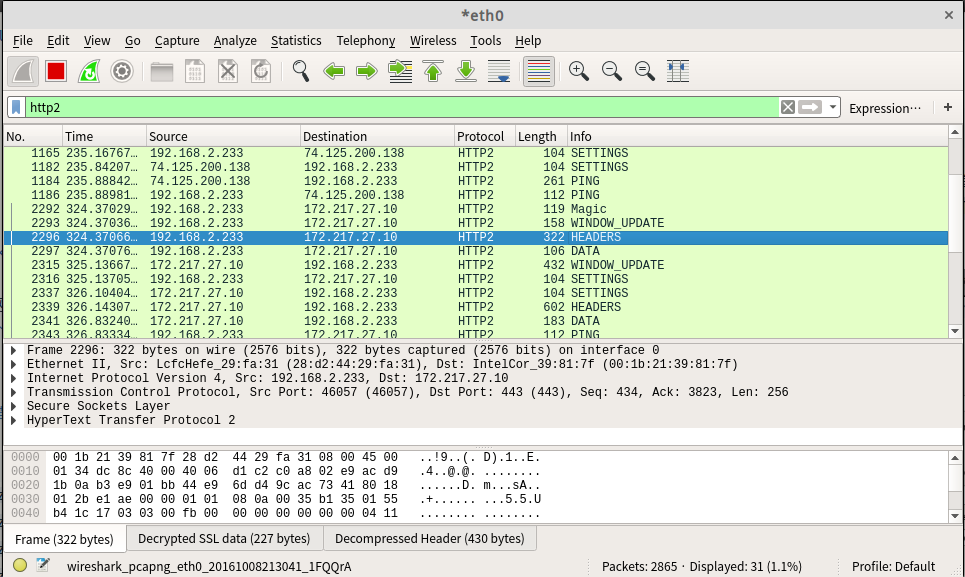
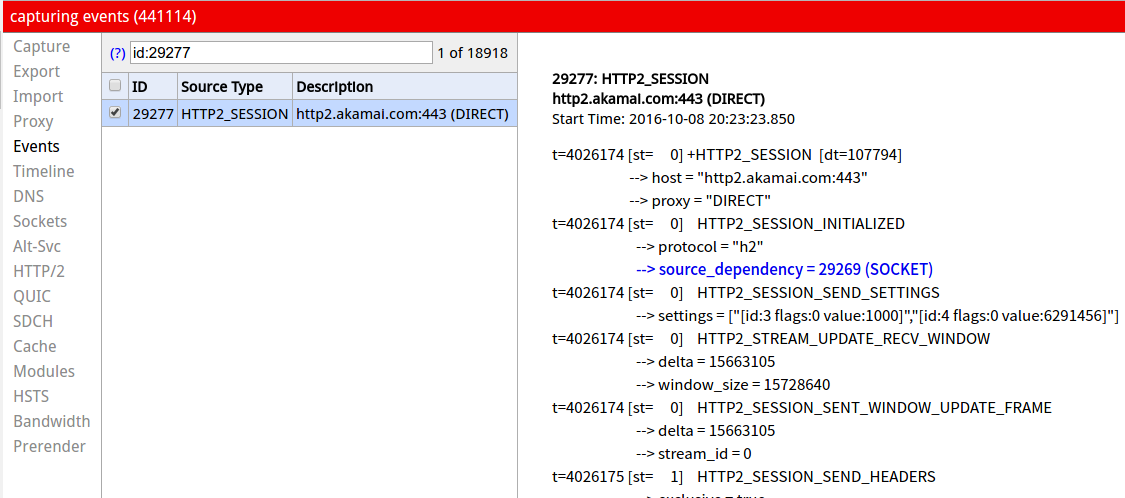
以 Chrome (版本:53.0.2785.143) 为例,通过其内置的 net-internals 工具(地址栏输入 chrome://net-internals/#http2)即可查看当前活跃的 HTTP/2 会话,通过选择对应的会话 ID 可以查看经过处理后的全部帧信息。
Wireshark
主流浏览器目前只支持 HTTP/2 Over TLS,HTTP/2 网站也都使用了 HTTPS,关于 HTTP/2 是否需要使用 TLS,曾经也有很大的争论,但是出于安全性和用户隐私的考虑,最后决定所有 HTTP/2 的数据传输都需要进行加密。
参见:
A lot of focus of http2 has been to make it behave properly over TLS.SPDY is only done over TLS and there’s been a strong push for making TLS mandatory for http2 but it didn’t get consensus and http2 will ship with TLS as optional. However, two prominent implementers have stated clearly that they will only implement http2 over TLS: the Mozilla Firefox lead and the Google Chrome lead. Two of the leading web browsers of today. Reasons for choosing TLS-only include respect for user’s privacy and early measurements showing that new protocols have a higher success rate when done with TLS. This because of the widespread assumption that anything that goes over port 80 is HTTP 1.1 makes some middle-boxes interfere and destroy traffic when instead other protocols are communicated there. The subject about mandatory TLS has caused much hand- waving and agitated voices in mailing lists and meetings – is it good or is it evil? It is an infected subject – be aware of this when you throw this question in the face of a HTTPbis participant! Similarly, there’s been a fierce and long-going debate on whether http2 should dictate a list of ciphers that should be mandatory when using TLS, or if it perhaps should blacklist a set or if it shouldn’t require anything at all from the TLS “layer” but leave that to the TLS WG.
最简单的方式是使用 NSS keylogging 配合 Wireshark (需版本支持)进行调试。
NSS(Mozilla Network Security Services)
是一组库目的是支持跨平台开发启用了安全性的多维客户机和服务器应用程序。用 NSS 构建的应用程序可以支持 SSL v2 和 v3,TLS, PKCS #5, PKCS #7, PKCS #11, PKCS #12, S/MIME, X.509 v3 证书,以及其他安全标准。
NSS 可以将密钥用特定格式写入日志(Key Log),这让外部程序得以借此解密 TLS 链接。Wireshark 1.6 版本以上可以用 Key Log 解密数据包。
Firefox 和 Chrome 只会在系统环境变量中存在 SSLKEYLOGFILE 路径时才会生成它,先来加上这个环境变量(以 Linux 为例):
export SSLKEYLOGFILE=~/保存地址/sslkeylog.log
这里保存至当前用户的 tls 目录下:
mkdir ~/tls
export SSLKEYLOGFILE=~/tls/sslkeylog.log
你也可以将其写入当前用户的 .profile 文件里,这样每次登录时该环境变量都会自动生效:
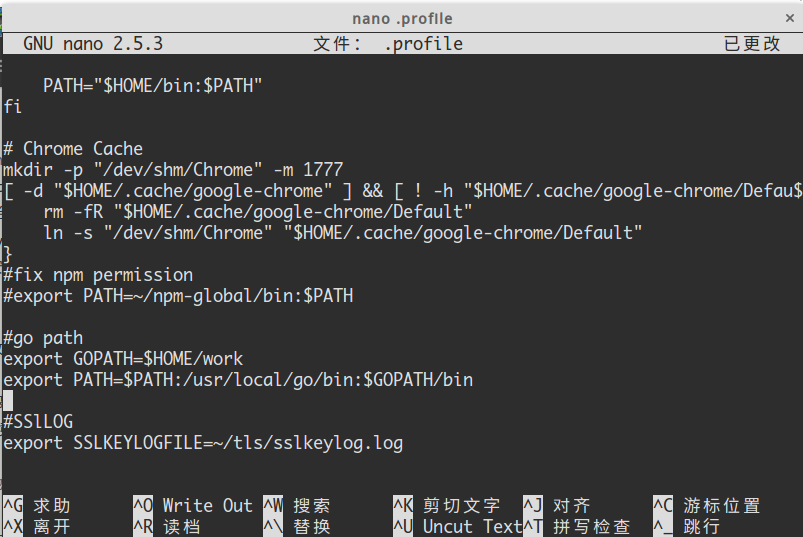
更新 profile:
source .profile
打开 Chrome:
google-chrome
启动 Wireshark:
sudo wireshark
接下来,选择监听网卡,打开 Wireshark 的首选项(preferences) ,点击协议(Protocols)选项,将 SSL 配置面板的 (Pre)-Master-Secret log filename 一栏中的文件替换成 sslkeylog 文件位置 即可:
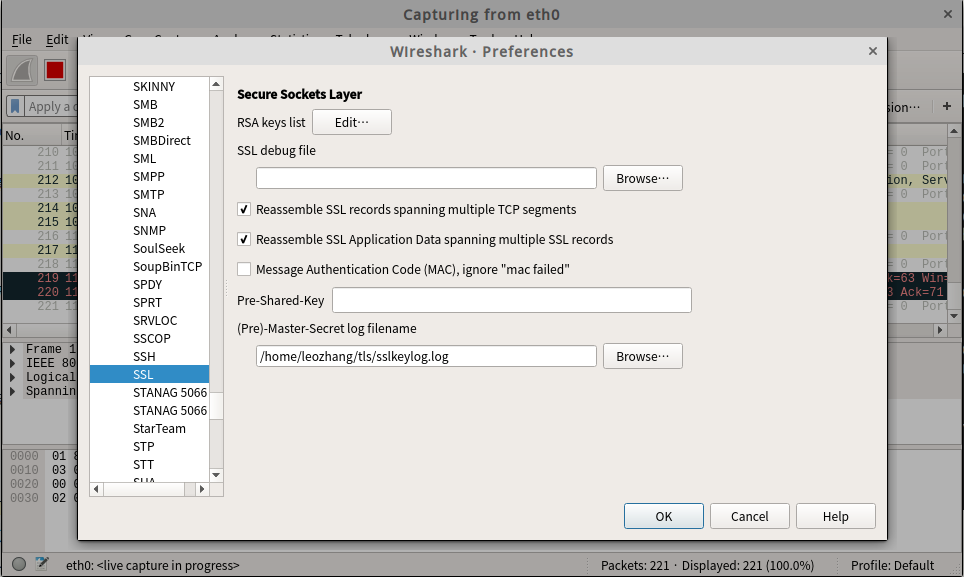
通过 filter 设置过滤规则,即可过滤出 HTTP/2 流量: